Tpm - Mantenimiento Productivo Total (TPM) » Ingenieria Industrial Online
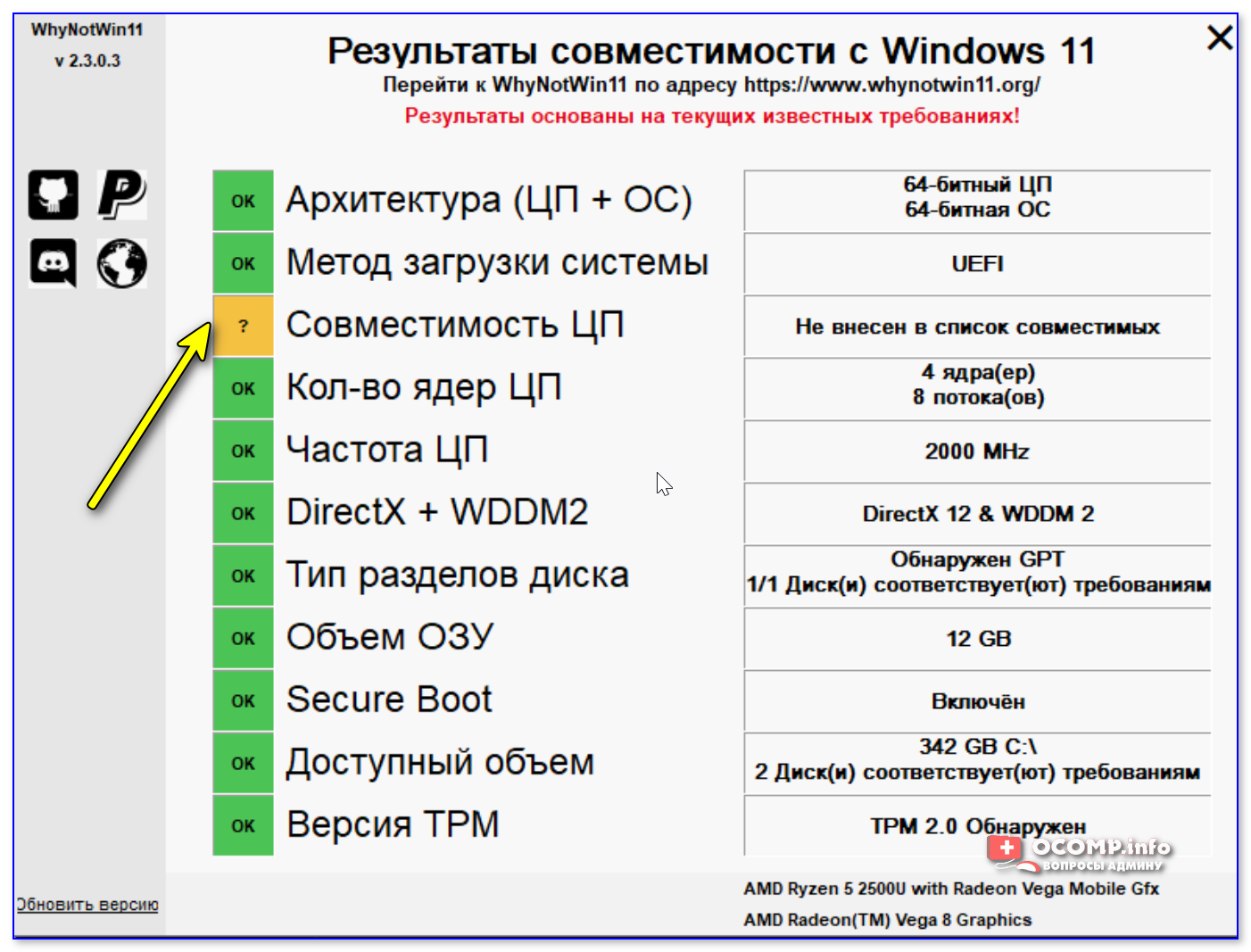
What is a TPM? And here's why you need it for Windows 11
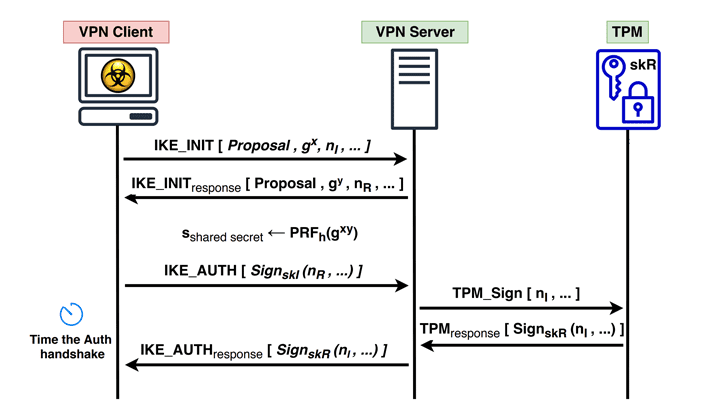
The chip includes multiple physical security mechanisms to make it tamper-resistant, and malicious software is unable to tamper with the security functions of the TPM.
Thanks to Windows 11, people are scalping TPM2.
In the search results, click on System Configuration.
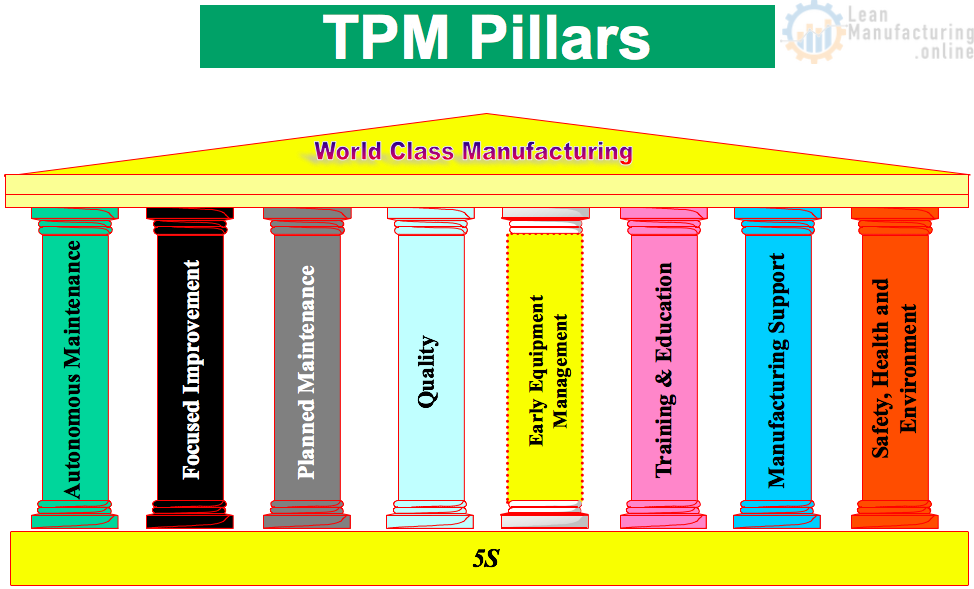
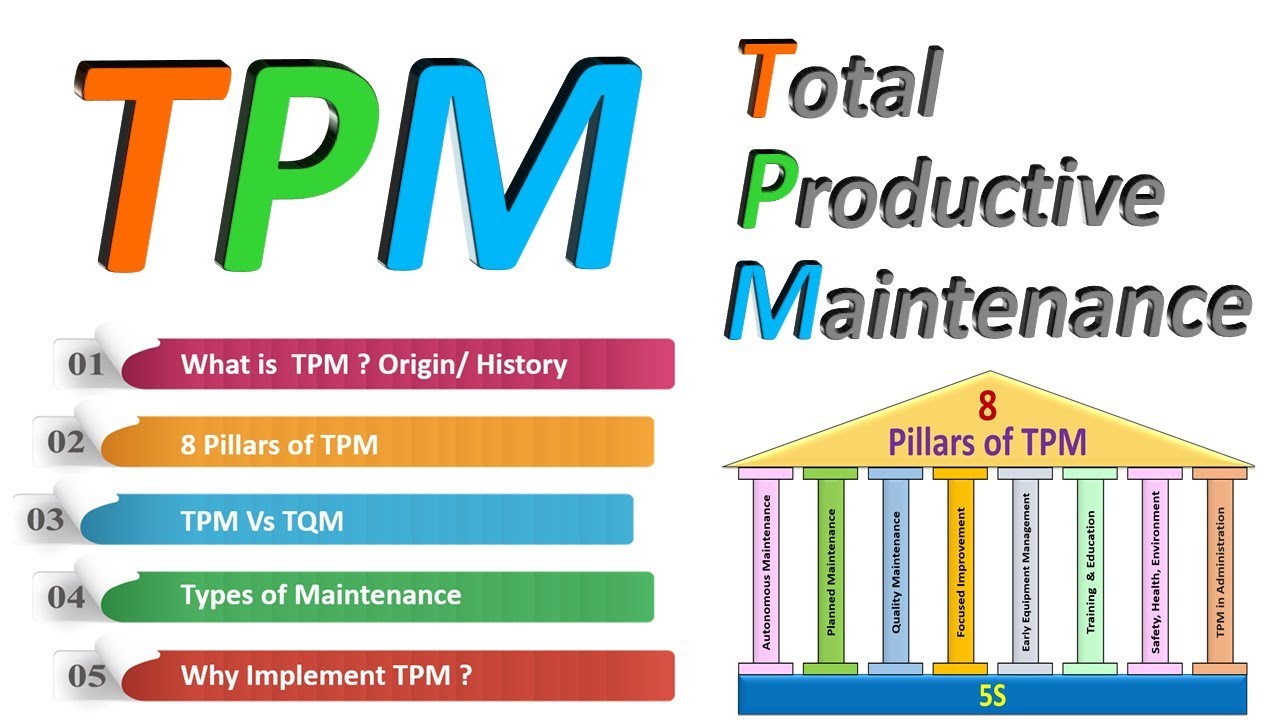
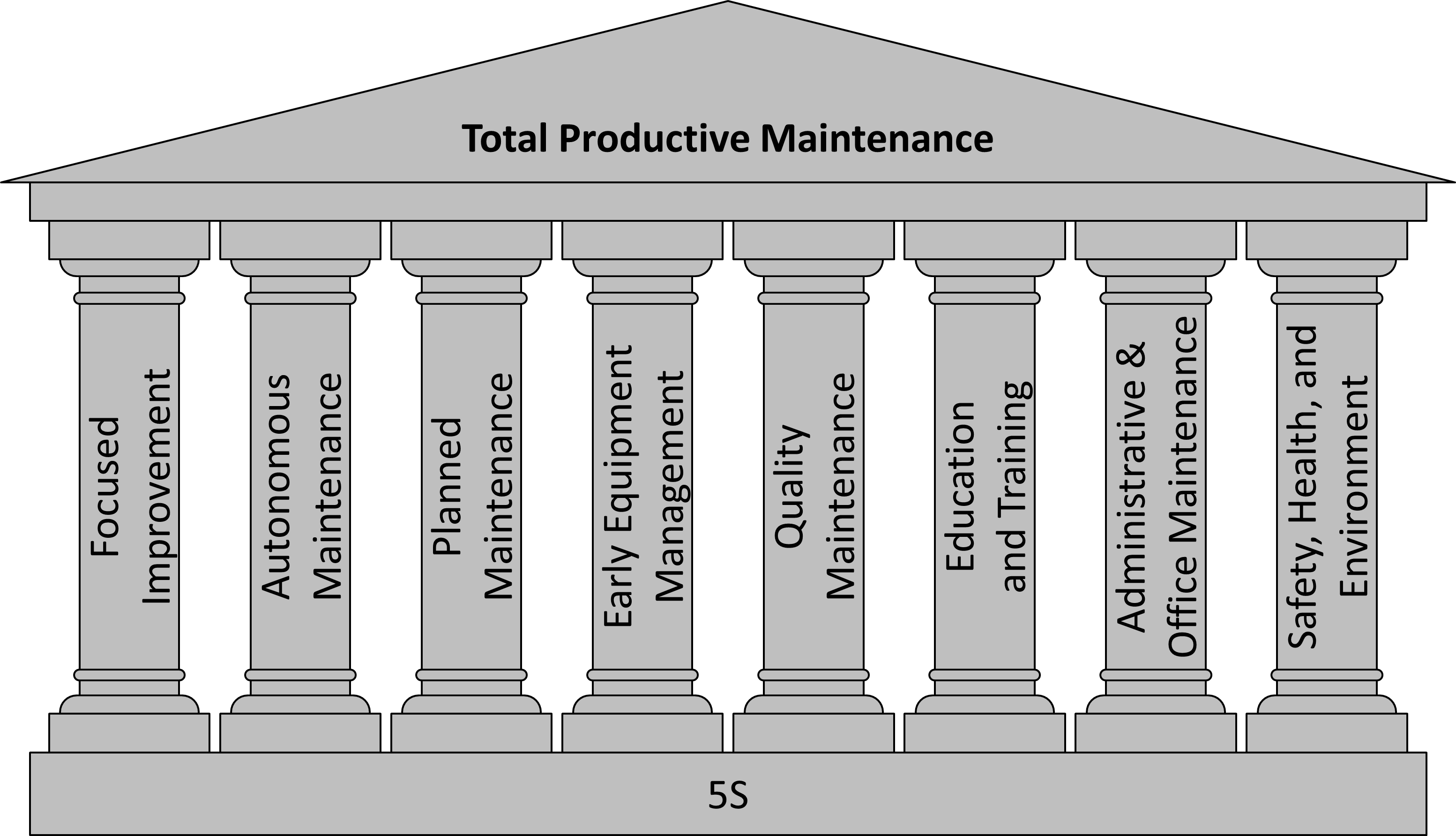
Total productive maintenance
Es importante que los operarios sean capacitados y polivalentes para llevar a cabo estas funciones, de tal manera que debe contar con total dominio del equipo que opera, y de las instalaciones de su entorno.
If you have a physical TPM module it will say so under, most likely, the security tab.
For example, the Unified Extensible Firmware Interface UEFI can use TPM to form a root of trust.
- Related articles
2022 mail.xpres.com.uy









.jpg)











