Phishing meaning in malay - Asia Law Portal
URL:Phishing
None of these is likely to work in isolation though and companies must develop a holistic approach that combines these components for a specific business context in order to best prevent phishing scams.
They also displayed names to use legitimate services.
These focus on the control of exports of military and technological goods to Russia and financial measures against Russian banks, entities and activities.
Phishing
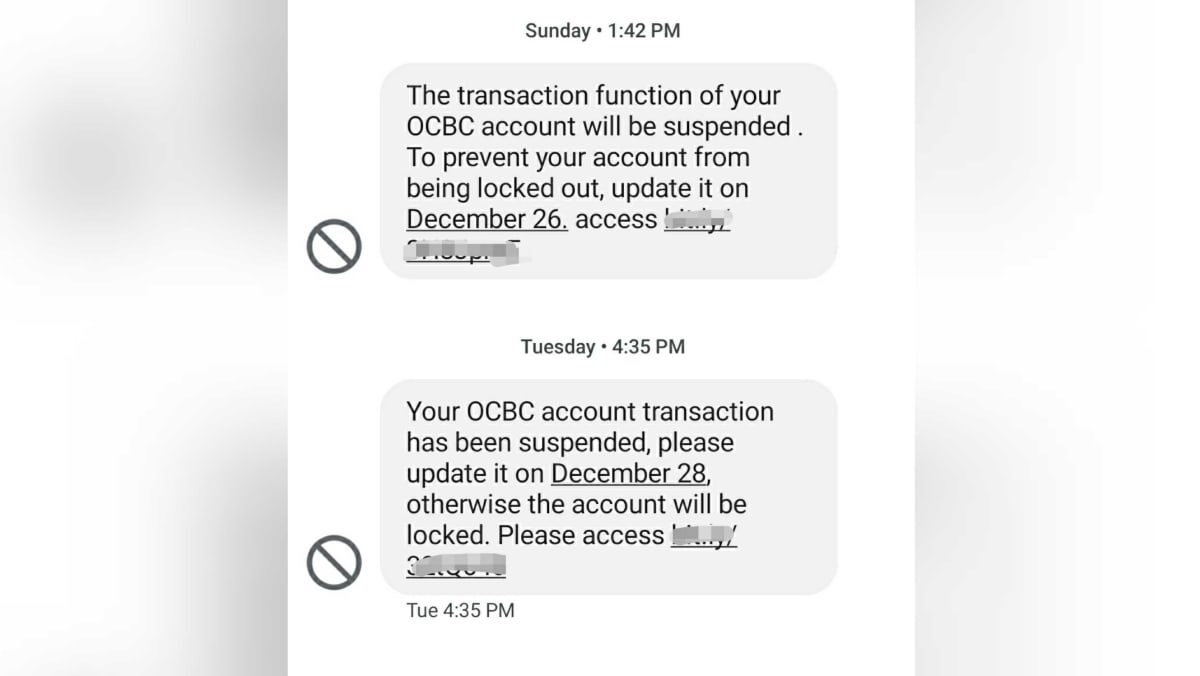
It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message.
Digital fraudsters show no signs of slowing down their phishing activity for the rest of the year, either.
These websites are designed to look like legitimate websites, such as those owned by a bank or company.
- Related articles
2022 mail.xpres.com.uy